5 Kali Linux tricks that you may not know
Posted in Articles on November 9, 2018
Posted in Articles on June 26, 2018

If you’re working on a challenge, vulnerable VM or CTF, you probably won’t know its IP address and won’t be able to get it with ifconfig because generally login credentials are not disclosed. So this is a basic tutorial on how to “guess” the IP address of a downloaded virtual machine that has DHCP enabled.
If you’re a seasoned pentester/bug bounty hunter/CTFer, this blog post is clearly not for you. It is addressed to anyone starting in InfoSec, whether you’re trying a first boot2root challenge or preparing for a job interview.
Why I am choosing this topic? Because everybody has to start somewhere. In my last corporate job, I created an intentionally vulnerable VM to assess the experience and technical level of applicants for a pentester job. The only information they had, was that the VM has DHCP enabled and their task was to find the maximum number of vulnerabilities.
To my surprise, many of them did not know where to start and asked for the IP address of the VM or the login credentials!
Here is how to retrieve your IP address (i.e. the IP address of your attack VM):
# ifconfig eth1
eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.4.4 netmask 255.255.255.0 broadcast 192.168.4.255
ether 08:00:27:f7:d2:c0 txqueuelen 1000 (Ethernet)
RX packets 1394 bytes 149194 (145.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 5276 bytes 347790 (339.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Then you can run Nmap to list all live hosts on the network:
# nmap -sn 192.168.4.1-254
Starting Nmap 7.70 ( https://nmap.org ) at 2018-06-20 15:51 WEST
Nmap scan report for 192.168.4.2
Host is up (0.0016s latency).
MAC Address: 08:00:27:30:07:F0 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.4.3
Host is up (0.0014s latency).
MAC Address: 08:00:27:AE:29:FE (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.4.4
Host is up.
Nmap done: 254 IP addresses (3 hosts up) scanned in 2.13 seconds
As you can see, in this example, there are 3 IP addresses on the Virtualbox Host only network:
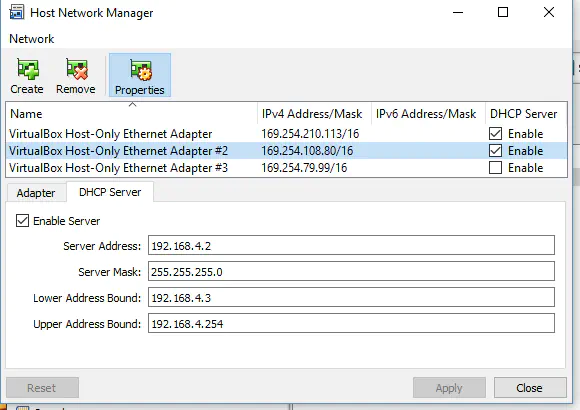
(*) Steps to get / modify the Host-Only network configuration:
Another tool for getting live hosts is Netdiscover. Instead of sending ICMP (ping) requests like nmap -sn does, it sends out ARP requests and returns which hosts responded:
# netdiscover -P -i eth1 -r 192.168.4.0/24
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.4.2 08:00:27:5a:06:db 1 60 PCS Systemtechnik GmbH
192.168.4.3 08:00:27:ae:29:fe 1 60 PCS Systemtechnik GmbH
-- Active scan completed, 2 Hosts found.
If you want to be sure, you can also port scan all your network. This is the easiest but slowest method since you’re scanning every open port on your network.
Intentionally vulnerable VMs will generally have more open ports than your own attack or desktop machines:
# nmap -n -sV 192.168.4.1-254
Starting Nmap 7.70 ( https://nmap.org ) at 2018-06-25 17:55 WEST
Nmap scan report for 192.168.4.2
Host is up (0.00027s latency).
All 1000 scanned ports on 192.168.4.2 are filtered
MAC Address: 08:00:27:5A:06:DB (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.4.3
Host is up (0.00035s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.5
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
MAC Address: 08:00:27:AE:29:FE (Oracle VirtualBox virtual NIC)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 192.168.4.4
Host is up (0.0000060s latency).
All 1000 scanned ports on 192.168.4.4 are closed
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 254 IP addresses (3 hosts up) scanned in 13.76 seconds
Now let’s get back to challenge solving!
Please let me know if you have a comment, other Nmap or Netdiscover tips, requests for tutorials, questions, etc.
See you next time!