Conference notes: How to fail at bug bounty hunting (LevelUp 2017)
Posted in Conference notes on July 19, 2018
Posted in Conference notes on July 25, 2018

Hi, these are the notes I took while watching the “Automation for Bug Hunters - Never send a human to do a machine’s job” talk given by Mohammed Diaa (@mhmdiaa) for Bug Bounty Talks.
This talk is about automation for bug hunters.
Boredom & drudgery are evil Hackers (and creative people in general) should never be bored or have to drudge at stupid repetitive work, because when this happens it means they aren’t doing what only they can do — solve new problems. This wastefulness hurts everybody. Therefore boredom and drudgery are not just unpleasant but actually evil.
Spending too much time on recon has been a mistake I’ve done in the past. By the time I start to hunt for bugs I would then be either too exhausted or bored to dig deep. - Mathias Karlsson (@avlidienbrunn), Bug Bounty Forum AMA
Google time filter
WaybackMachine (or WaybackUnifier, a wrapper around Waybackmachine)
Old mobile app versions
Monitor the following for changes or updates:
Example of workflow to help familiarize you with the concept of chaining tools:

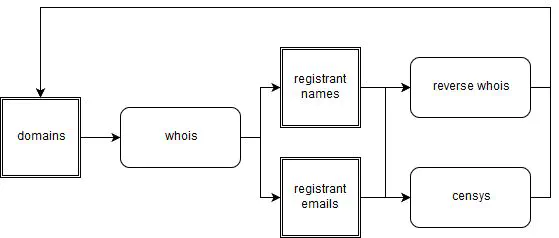

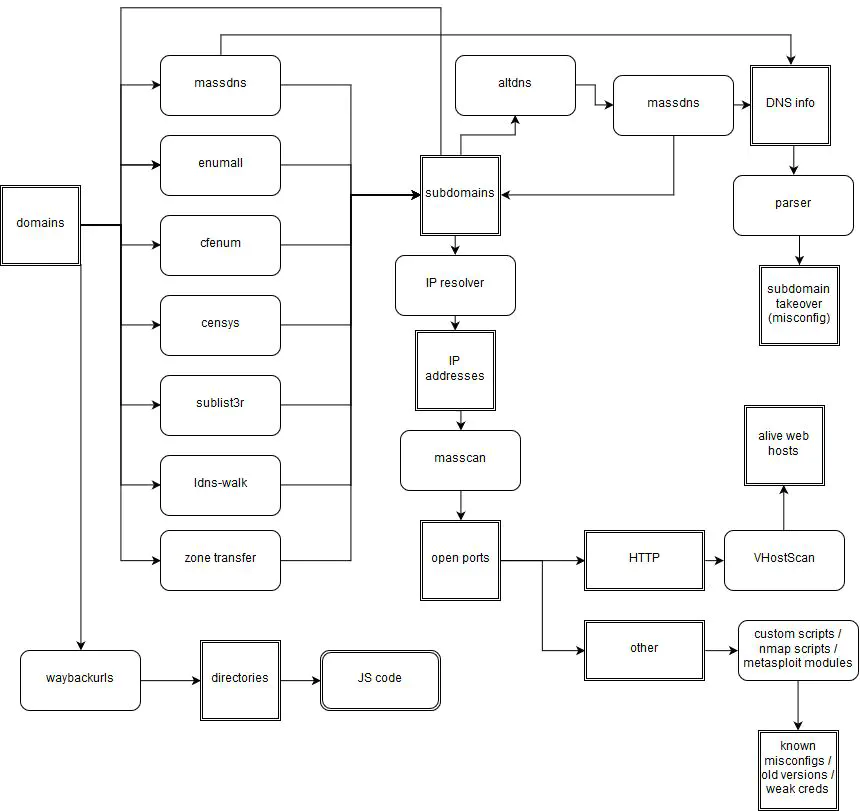
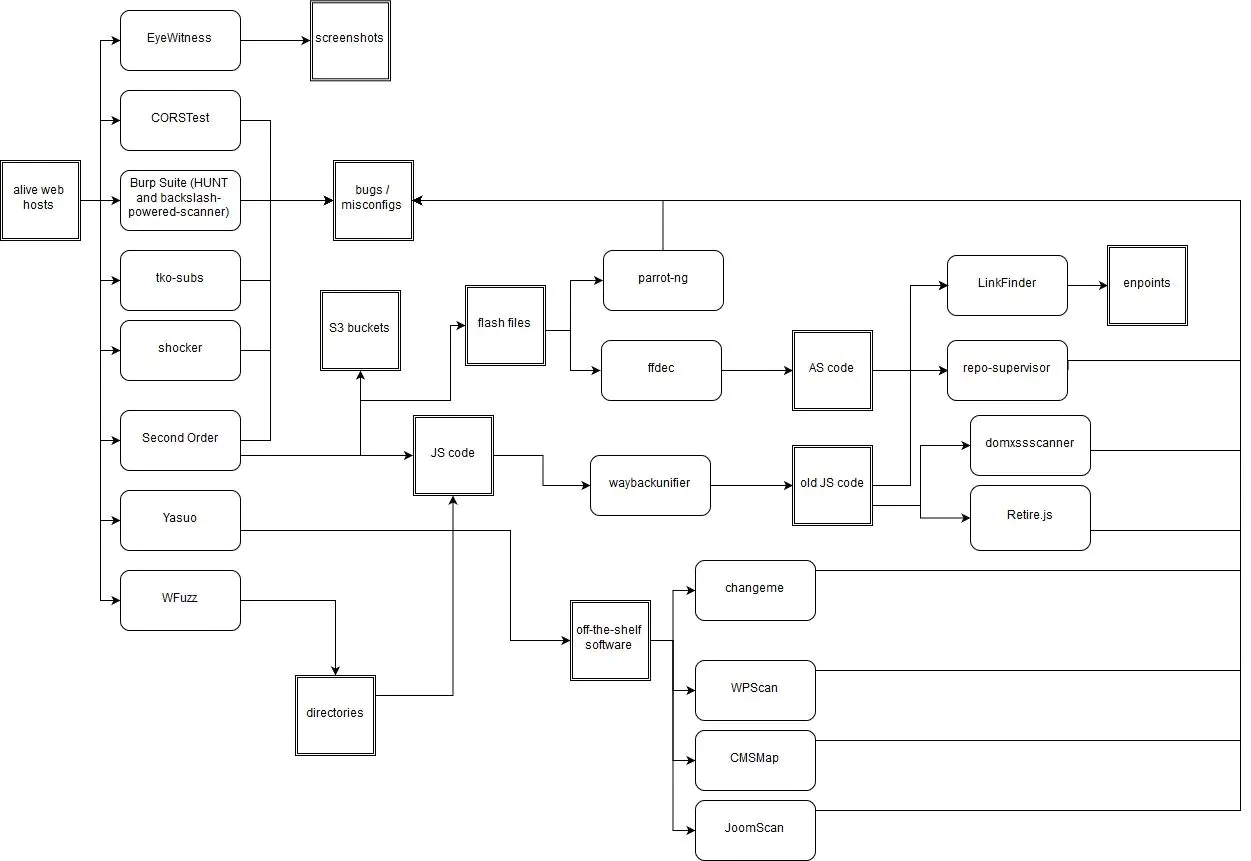
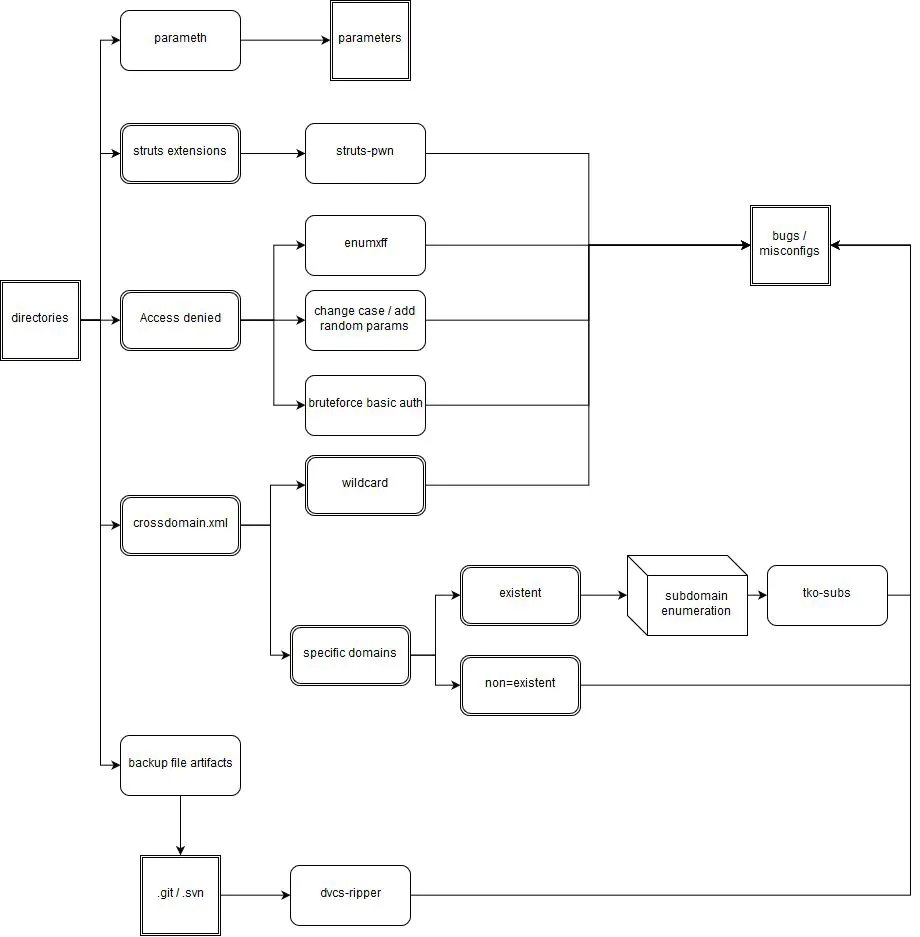
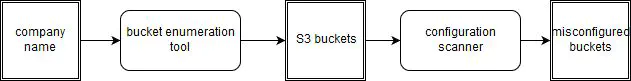
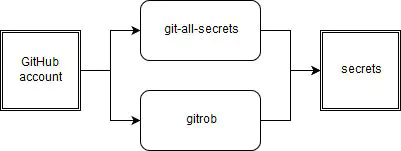
What we do wrong: Rebuild existing tools too often
Why?
If your new tool isn’t helpful, you’re probably wasting time
Focus more on building new tools and extending existing ones
List of existing tools: https://bugbountyforum.com/tools/
List of tools we need: https://ideas.bugbountyforum.com
See you next time!