Conference notes: Practical recon techniques for bug hunters & pen testers (LevelUp 0x02 / 2018)
Posted in Conference notes on October 17, 2018
Posted in Conference notes on November 7, 2018

Hi, these are the notes I took while watching the talk “How to Differentiate Yourself as a Bug Bounty Hunter” given by Mathias Karlsson at OWASP Stockholm.
This talk is about how to differentiate yourself from the crowd, to ensure that you are successful at doing bug bounties.
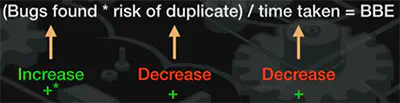
Bug Bounty Effectiveness (BBE) formula:
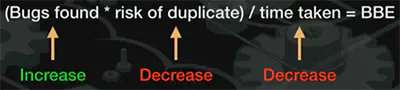
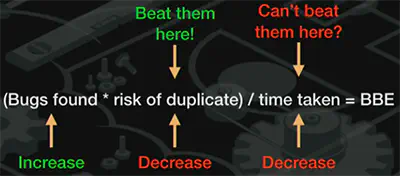
3 underrated ways of achieving BBE:
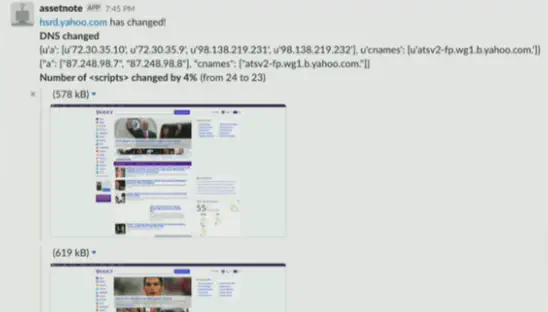
Bonus: Accidental bug find
/shudown shuts down the server (Denial of service, $12,000)During your recon process:
Also:
But:
Note: I’m paraphrasing here, not reporting exact quotes…
Q: Have you ever hit backlists when monitoring targets & got yourself blocked out because you were monitoring too hard or too often?
A: My monitoring is very gentle. It happens but not often. I don’t run tools like Nessus. I only send a few HTTP requests per day. They’re spread out over time
Q: [not clear, I understood something like: can you still hack a target even if they’re using a WAF?]
A: WAFs are really good at blocking automated attacks but not manual ones. If I detect a WAF, I either give up because it’s a waste of time or figure out a way around it. Many times, it’s possible
Q: Do you do recon against the employees of your target? For example, trying to figure out what their programming style is based on what they published on public personal accounts
A: yes, that’s what a real attacker would do
Q: Did you ever go out of scope & make someone upset?
A: It’s happens but accidently. Programs are pretty understanding, I never got into real trouble
See you next time!