The 5 Hacking NewsLetter 33
Posted in Newsletter on December 25, 2018
Posted in Newsletter on July 9, 2018

Hey hackers! Here are our favorite resources for penetration testers and bug bounty hunters for last week (June 29 to July 6).
I loved watching this podcast! The story of Bull (@v0sx9b) is impressive: he’s a self-taught full-time bug bounty hunter since only 2016 and already making a lot of money. So it’s good to listen to his hunting philosophy and tips.
For example, he focuses on big bugs and doesn’t report small ones, but rather keeps them to chain them and report higher impact bugs. This way, he reports 6/7 bugs a month on average but with high criticality & reward.
This is a handy tool for bug hunters. It’ll allow you to quickly grab all publicly disclosed reports of any HackerOne program you are working on.
The $12,000 Intersection between Clickjacking, XSS, and Denial of Service by Sam Curry
This is a great write-up on how to find high reward bugs on a target that has been tested by hundreds or thousands of other researchers. The tricks mentioned include:
This is a new mailing list started by EdOverflow. You can browse the archive and read many good tips for bug hunters like how to escalate stored XSS for a better reward, great subdomain takeover tricks, etc.
Both the contents and the design of this poster are great. It sums up all the excuses I heard from clients as an internal security auditor then pentester.
The first time I saw it, it made me laugh and feel comforted because I felt less alone in this fight against the false obstacles and excuses.
You can find the latest bug bounty writeups in our dedicated page: List of bug bounty writeups.
Only writeups that did not make it to this selection are listed below. This does not mean that they aren’t worth reading, just that they are not BUG BOUNTY writeups. We will soon post more details about how our curation process.
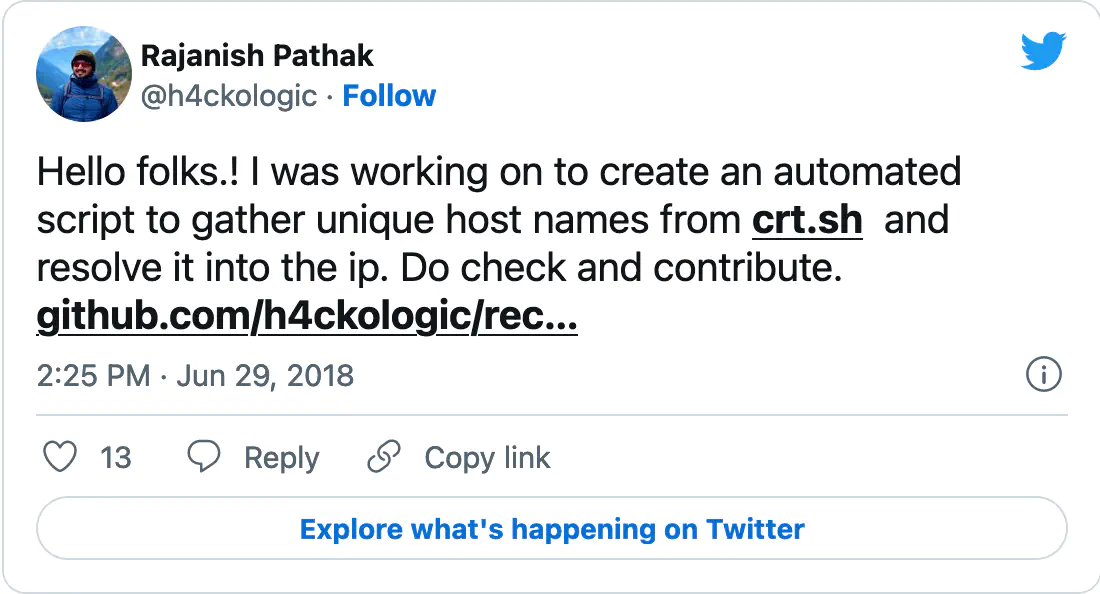
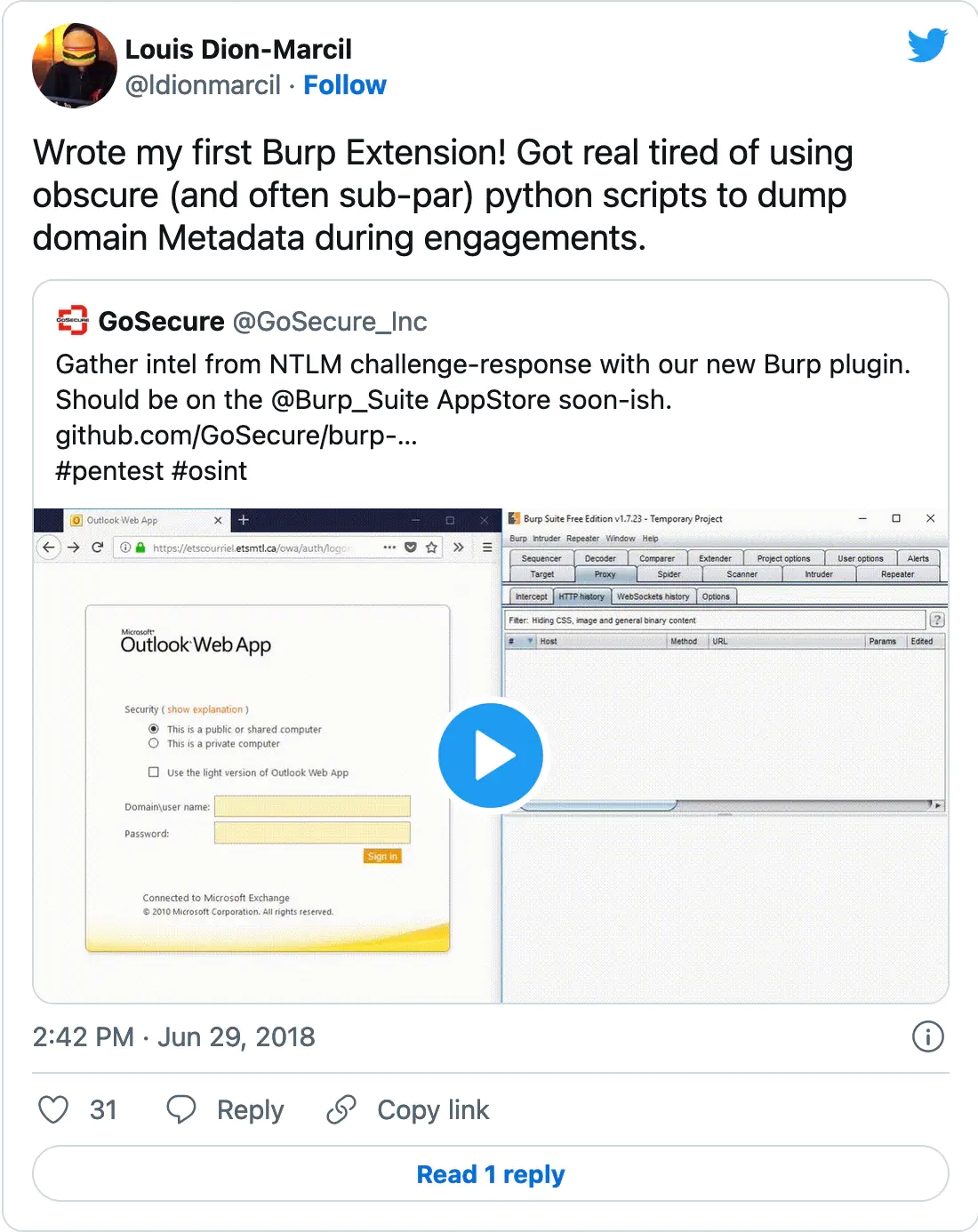
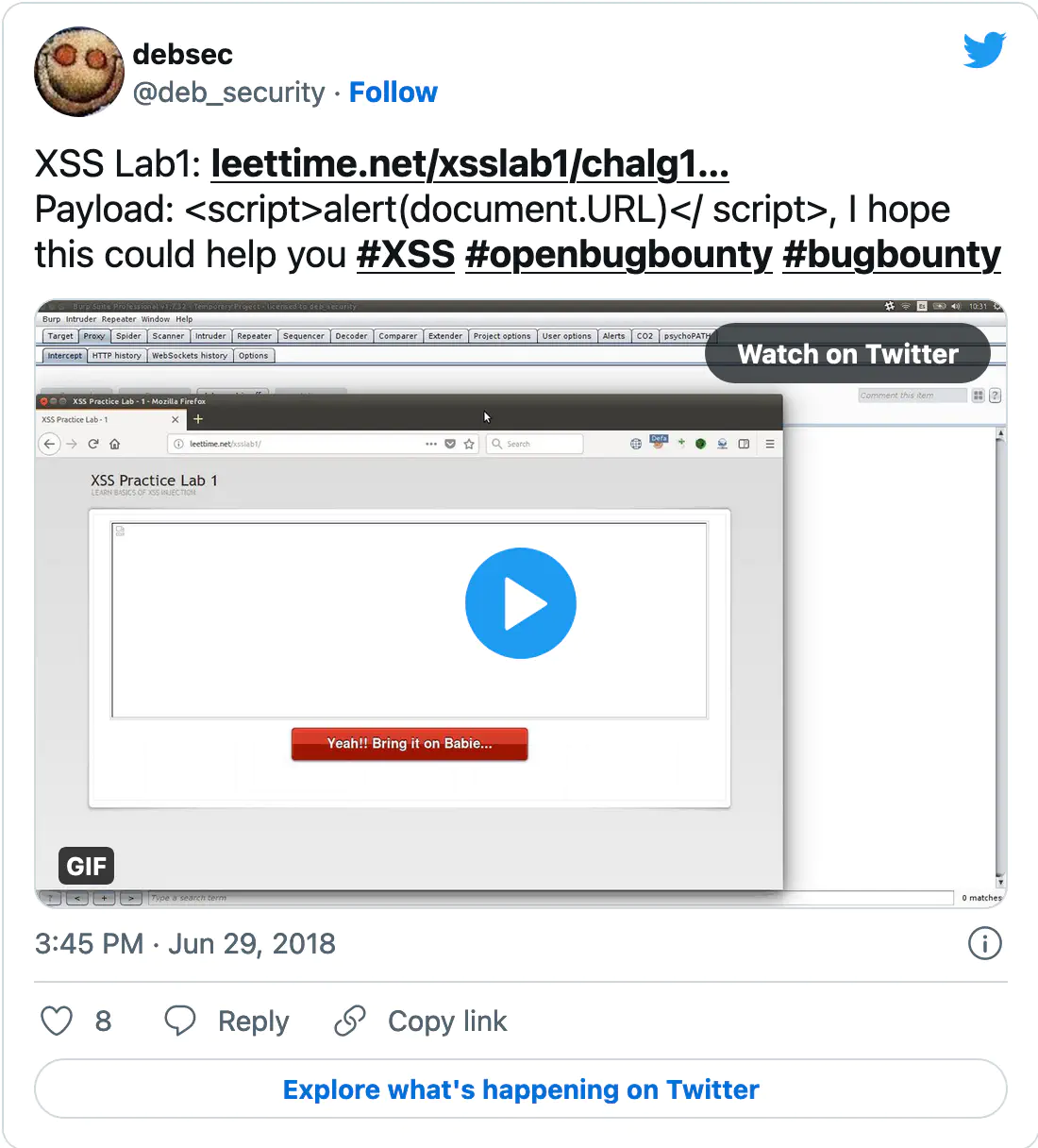
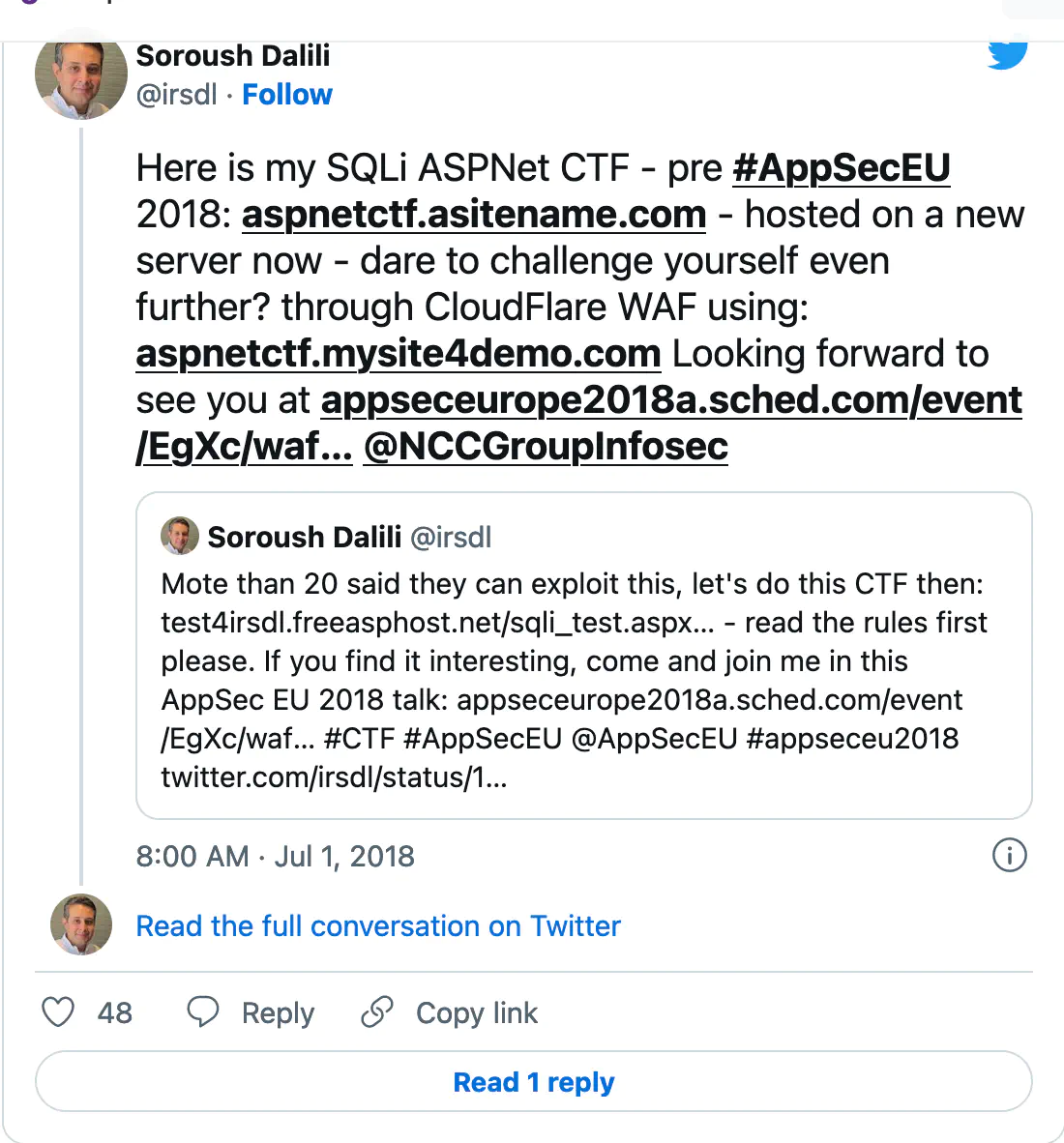
We created a collection of our favorite pentest/bug bounty related tweets shared this week. You’re welcome to read it directly on Twitter.
Have a nice weekend folks!
If you enjoyed reading this, please consider sharing it, leaving a comment, suggestions, questions…