Conference notes: Eliminating False Assumptions in Bug Bounties (OWASP Stockholm 2018)
Posted in Conference notes on March 14, 2019
Posted in Conference notes on March 8, 2019

Hi, these are the notes I took while watching the “API Security 101” talk given by Andy Sadako on LevelUp 0x03 / 2019.
This talk covers the basics of API security testing for hackers.
&admin=True or &test=1Depending on the app’s architecture, specific parts of a request may be processed in unsafe ways (applies to any web app whether it’s an API or older app) including:
If an attacker supplies multiple parameters named SAMLResponse, the signature is verified against the last occurrence of the parameter, while the SAML response that is processed further, will be taken from the first occurrence
&user=Andy&user=Sam => &user=Sam is used for signature but after that the app uses the first parameter &user=Andy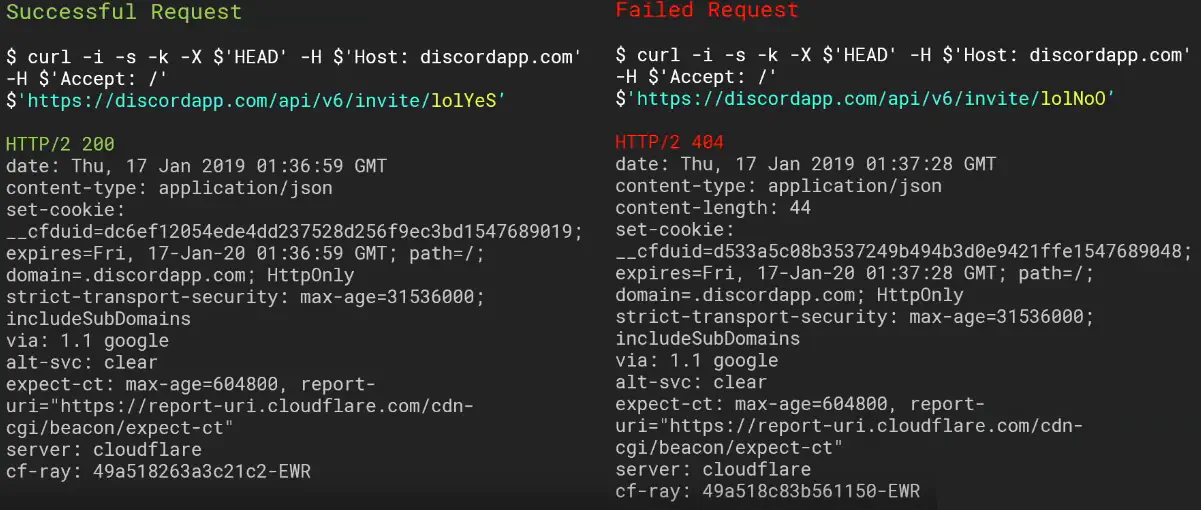
mobile.dudasite.com/site/<sitename>/default?url=<externalUrl>Andy’s email address: blackhat[at]zipcar[dot]com.
See you next time!